I am thrilled to announce that Bitdefender has released a remarkable decryption tool for the Revil/Sodinokibi ransomware. You can easily download it from the following link: https://www.bitdefender.com/blog/labs/bitdefender-offers-free-universal-decryptor-for-revil-sodinokibi-ransomware/.
Recently, I successfully utilized this tool to recover 100% of the data from a client’s encrypted hard drive, even though it had been 9 months since the initial attack. This attack was possible due to a successful compromise of the user’s password via Remote Desktop. To ensure the safety of your remote computer access, I highly recommend changing the default port (3389) to a more obscure one and strengthening your password.
The impact of the attack went beyond encrypting the client’s local hard drives; it also affected their backup drives. To detect any unusual behavior, I advised the client to power off the PC when not in use, but unfortunately, this precaution was not taken. Since then, we have implemented various data recovery techniques, including weekly swapping of backup drives enabled by Storagecraft’s ShadowProtect software. Fortunately, we had recently replaced the main drive, which had a growing number of bad sectors, allowing us to fully restore all data with a 100% success rate. By comparing the current and encrypted drives, we were able to analyze the differences and develop a comprehensive methodology for recovering deleted files, which could potentially be explored in a separate blog post.
When it comes to restoring and merging the client’s data with their existing setup, it’s important to note that relying on the date created and modified is not feasible, as these change during encryption and decryption. Therefore, a direct file and directory comparison between the two drives is necessary for an accurate restoration process.
Why is this Tool Essential for Data Recovery?
In June of this year, REvil targeted eight MSPs (Managed Service Providers) who relied on the indispensable Kayesa remote management tool to administer their outsourced IT services. Despite a vulnerability in Kaseya servers being on the brink of being patched, the REvil ransomware gang swiftly executed their attack in July, just moments before the patch was applied.
The assault coincided with America’s 4th of July weekend, as REvil partners exploited a vulnerability in the Kaseya VSA remote management service, utilized by approximately 35,000 customers. Leveraging their control over Kaseya’s servers, they cunningly distributed a compromised software update to the unsuspecting customers of Kayesa, predominantly small and medium-sized enterprises (SMEs).
The repercussions of this attack were nothing short of catastrophic, widely impacting companies across the globe. For instance, the renowned Swedish supermarket chain, Coop, was forced to close nearly half of its 800 stores due to the malfunctioning checkouts caused by the attack. Similarly, schools, kindergartens, and public administration offices in New Zealand and Romania suffered from its devastating consequences.
Gain insights into this cyber catastrophe through the map below, showcasing the infected computer systems as observed by the esteemed cyber-security firm, Kaspersky.
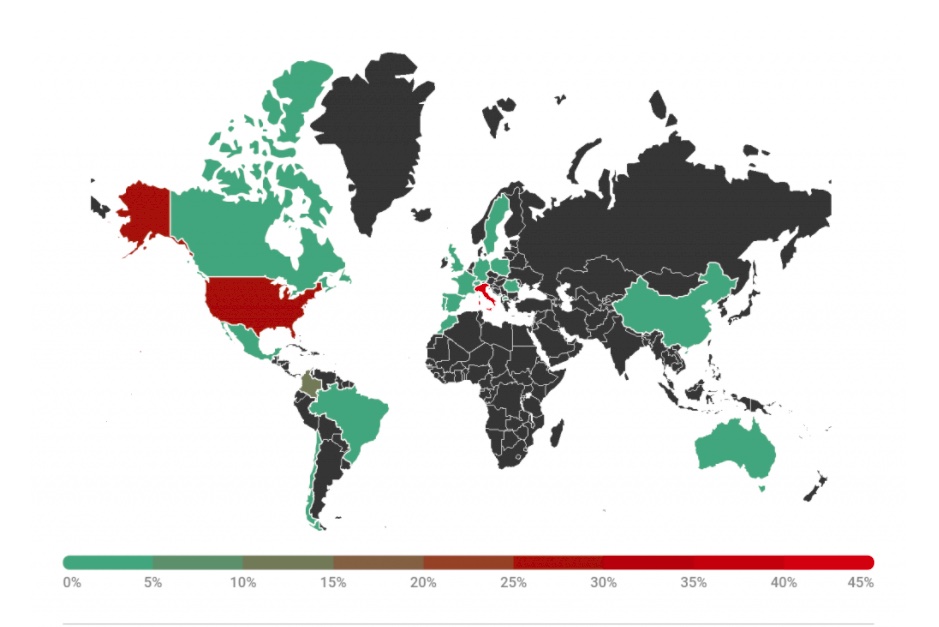
While the Revil groups website has disappeared from the dark web , the prevalence of remote attacks has increased with the Covid 19 pandemic and I am increasingly attempting to recover data from encrypted drives. This type of threat is not going to disappear and the adage prevention is better than the cure is definitely true. Data Recovery on encrypted drives can be painstaking.
Some of our Reviews
REQUEST A QUOTE
Address
126 Whatley Crescent Maylands
call:(08) 6180 6959
126 Whatley Crescent
6 Days a week from 8:00am – 5:00pm
